LogCraft CLI 0.1 General Availability (OpenSource)
We are excited to announce the release of LogCraft CLI 0.1 into General Availability. Security practitioners can now easily build Detection-as-Code pipelines in their favorite version control systems such as GitLab and automatically deploy their detections in their favorite SIEM, EDR, XDR, or anything with an API.
What is LogCraft CLI?
Today, we announce LogCraft CLI, a tool for safely and efficiently validating, building, and deploying security detections into modern security tools such as EDR, SIEM, XDR, and anything with an API.
With LogCraft CLI, you describe your detections as code, even as they span multiple detection technologies. Your SIEM may come from Splunk, your EDR may come from Tanium, or you may have multiple SIEM solutions from different vendors. LogCraft CLI will build and deploy these detections across all these providers.
LogCraft CLI codifies knowledge about your security detections unlike any other tool before and provides the workflow and tooling for safely changing and updating modern security tools.
We are excited to release LogCraft CLI and what we have for you today is just the beginning.
Read on to learn more.
How it works?
This brief explanation of how LogCraft CLI is used and operated will show how simple and powerful LogCraft CLI is. Many technical details are omitted on purpose, as they are covered in detail in the documentation.
LogCraft CLI describes detections, one per file, in YAML format. An example of such a detection, a Splunk search, is shown below.
name: High Entropy Domain (DGA)
rules:
splunk:
app: SA-MyApp
savedsearch:
search: |-
index=main sourcetype=proxy url=*
| eval list = "mozilla"
| `ut_parse_extended(url, list)`
| stats sum(count) as count values(src_ip) by ut_domain
| `ut_shannon(ut_domain)`
| search ut_shannon>3
cron_schedule: 10 0 0 0 0
disabled: True
description: |-
This detection alerts on high entropy domain name often the sign
of domain generated algortihm (DGA).
action.correlationsearch.annotations: |-
{
"mitre_attack": ['TA0011', 'T1071.004'],
...
}From this human-readable file, LogCraft CLI (lgc) will:
- Validate parameters before they reach the remote system. For example, the "disabled" parameter in Splunk expects a boolean value. If anything other than a boolean is provided, an error will occur. By adding data types, similar to software engineering, we enhance the reliability of any security tool. 💪 See lgc validate
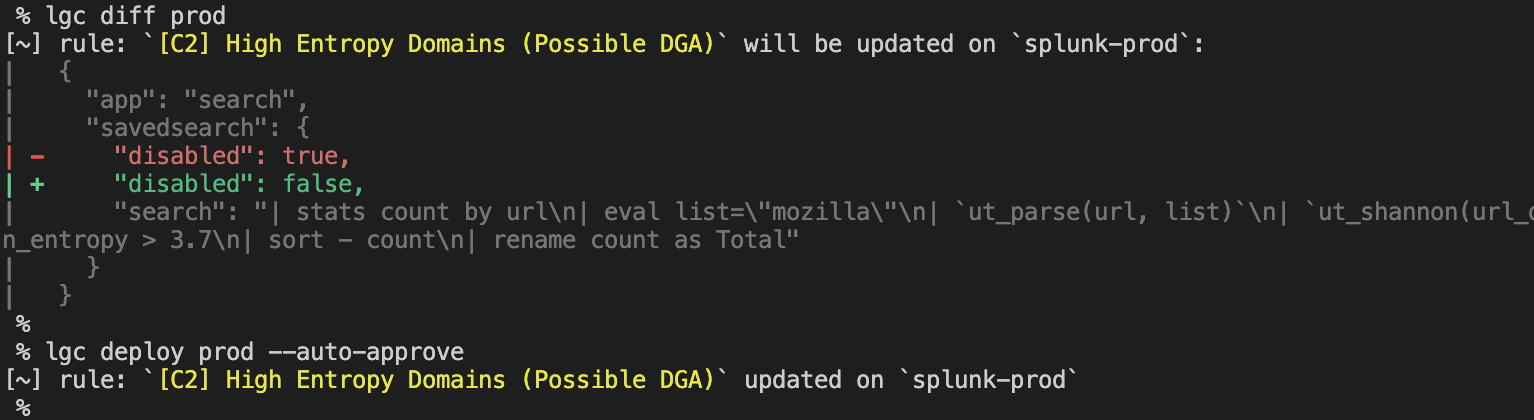
- Identify the differences between what is currently deployed and what should be deployed, effectively eliminating configuration drift. See lgc diff
- Automatically deploy and remove detections with a single command, see lgc deploy.
Plugin framework
LogCraft CLI also includes an efficient and fast universal plugin interface that allows the creation of plugins for any SIEM, EDR, XDR, or anything with an API, without compromising on safety and execution speed due to its memory-safe, sandboxed architecture.
Plugins can be created in virtually any language such as Go, Python, Rust, or C/C++.
LogCraft Platform
LogCraft Platform is a Detection-as-Code management platform that simplifies and accelerates the security detection development cycle from idea to production. By integrating LogCraft CLI, it provides advanced features that improve collaboration between security teams, strengthen operational processes, and scale with your team.
Features include peer review, documentation, deployment approval, MITRE ATT&CK analysis, TLP filtering, and more!
Contact us for a free demo or visit https://www.logcraft.io